Stop Protecting Systems, Start Protecting Data
data-security security-strategy data-protection
The short version: We spend fortunes protecting servers and networks, but the data is the actual asset. Modern security strategy must follow the data: know where it lives, how it moves, who touches it, and how long it should exist. AI makes this urgent: your data is now training material.
Your network perimeter? Not the asset.
Your servers? Not the asset.
Your fancy new firewall? Definitely not the asset.
The data is the asset. And we’re still acting like it’s not.
We’re Having the Wrong Conversation
Twenty years into my cybersecurity career, NSA, two CISO roles, ransomware battles at scale, and I’m still hearing the same thing:
“Our data governance project didn’t get funded. They said it’s not critical.”
Not. Critical.
The actual thing attackers want? Not critical.
The thing regulators fine you for losing? Not critical.
The thing your customers trusted you to protect? Not critical.
But sure, let’s drop another six figures on endpoint protection.
AI Just Made This Urgent
AI isn’t coming. It’s here. And it’s eating data faster than most organizations can track it.
Companies are deploying AI tools without asking basic questions:
- What data are we feeding these systems?
- Who can access the outputs?
- Where did this training data come from?
- Has it been poisoned?
You can’t secure what you don’t understand.
And right now? Most organizations don’t understand their data at all.
Five Questions You Can’t Answer (But Need To)
What data do we have?
Not “what systems.” What data, across every SaaS app, cloud bucket, employee laptop, and AI training set.
Who has access?
Not what your IAM dashboard says. Who actually has access, including that contractor from 2019 and the service account nobody remembers creating.
What systems have access?
Your APIs are chatting. Your applications are sharing. Your AI tools are consuming. Can you map those flows?
Where did it come from?
Data lineage matters. When something breaks or leaks, can you trace it back? Or are you guessing?
Has it been tainted?
Data poisoning is real. Corrupted sources are real. If you can’t validate integrity, you can’t trust anything downstream.
Can’t answer these? You have a problem.
Using AI? That problem just became critical.
Sell It or Watch It Fail
Here’s the uncomfortable part: it’s our job to make leadership care.
Not to complain about budget. Not to accept “not critical” and move on.
To build the case. To show the risk. To make it impossible to ignore.
Because systems-first thinking is dead. The attackers moved on years ago.
They’re not trying to breach your firewall anymore. They’re after your data.
And they’re betting you haven’t protected it.
What Data-Centric Actually Means
- Discovery first. Can’t protect what you don’t know exists.
- Classification as security. Don’t know what’s sensitive? Every breach is catastrophic.
- Access as continuous validation. Trust expires. Verify constantly.
- Data flows = attack paths. Map the data, map the threat.
This isn’t a project. It’s a fundamental shift in how you think about risk.
The Bottom Line
Systems matter. Of course they do.
But if you’re still putting infrastructure before information, you’re fighting the wrong battle.
AI accelerated the timeline. The threat landscape evolved.
The organizations that get this, that recognize data as the primary asset, not an afterthought, those are the ones that survive.
So stop accepting “not critical.”
Ask the five questions. Build the case. Shift the conversation.
Because the attackers already shifted theirs.
They’re coming for your data.
What are you doing to stop them?
Need help building a data-centric security strategy? Virtual CISO services provide the strategic leadership to shift your organization from systems-first to data-first thinking. Get help with data classification, access governance, and making the business case for data protection initiatives.
Book a free consultation to discuss your data security priorities.
Connect with me on LinkedIn for more insights on data-centric security.
Ready to Secure Your Growth?
Whether you need an executive speaker for your next event or a fractional CISO to build your security roadmap, let's talk.
Consulting services are delivered through Vaughn Cyber Group.
Related Posts

When Everything Is Critical, Nothing Is Critical
Your vulnerability scanner flagged 10,000 issues. Your SIEM has 500 critical alerts. Every project is top priority. So what do you actually fix first?
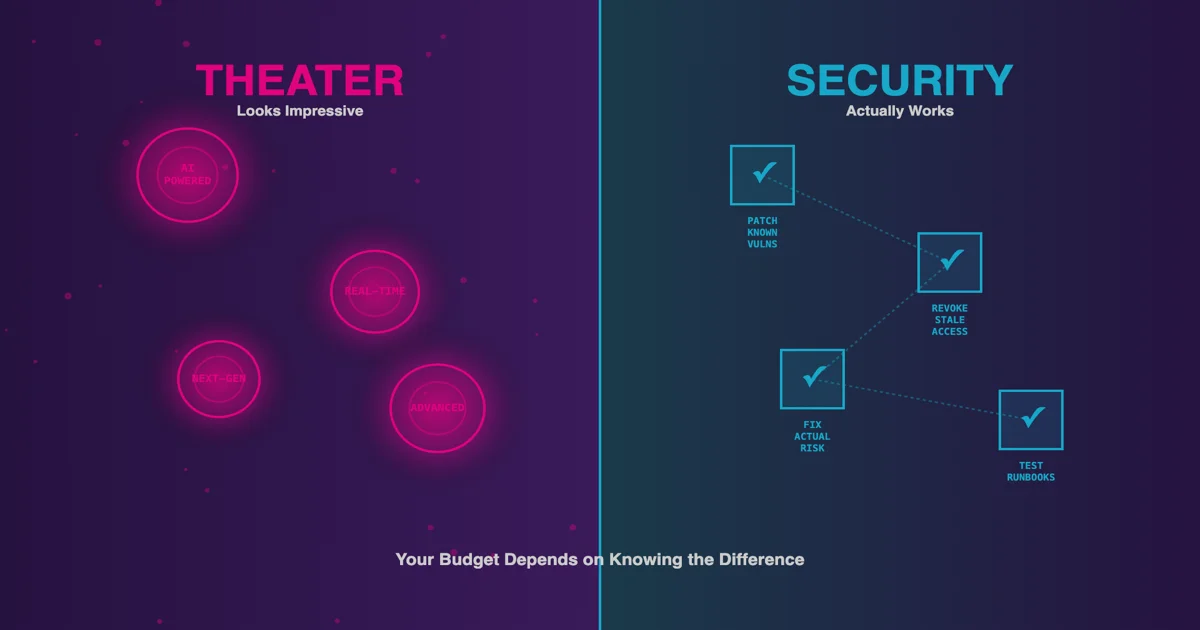
Security Theater vs. Security: How to Tell the Difference
That shiny new security tool looks impressive in the demo. But will it actually reduce risk? Here's how to tell security theater from real security before you waste the budget.

From Jewels to Data: Why We Never Learn
The Louvre got robbed. Companies get breached. Both could've been prevented. Here's why waiting for the 'oh crap' moment is a terrible security strategy.
