The Question That Made Everyone in the Room Go Silent
incident-response cybersecurity security-leadership
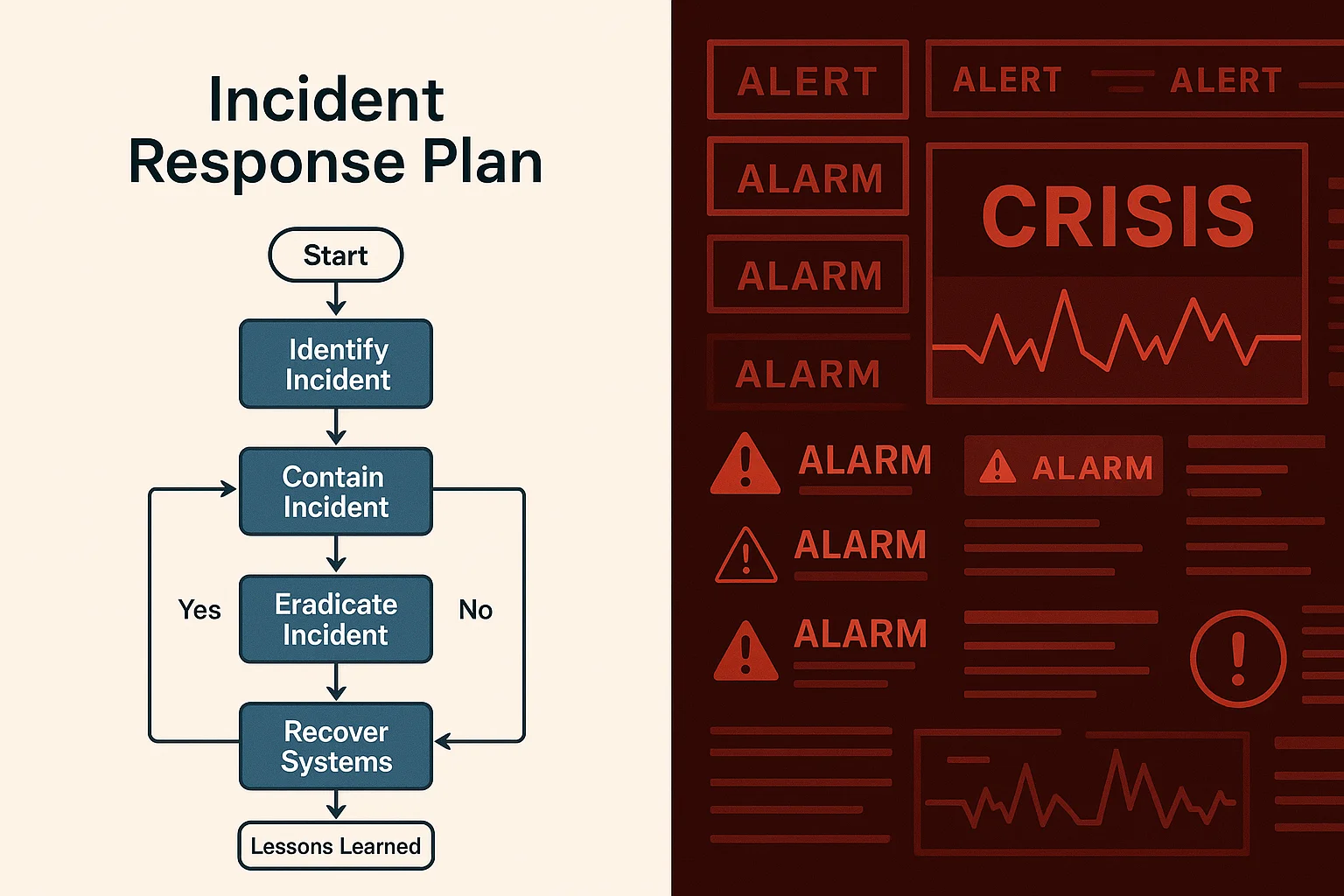
The short version: Most IR plans look great until you actually need them. The plan breaks when the right person is unreachable, when the backup isn’t as isolated as you thought, or when reality doesn’t match your assumptions. Test with realistic chaos, not scheduled exercises.
Earlier this year, I asked a simple question in a room full of cybersecurity professionals. The silence that followed was… telling.
“Raise your hand if you’ve actually used your incident response plan during a real, major incident.”
Hands went up for “we have a plan” and “we test regularly.” But when I got to the actual using part? Crickets.
The few hands that stayed up? When I dug deeper, those stories got… interesting.
The Moment Everything Changes
There’s a moment in every major incident where you realize the plan you’ve been so confident about is suddenly useless. Maybe it’s when you discover the person who knows the recovery process is unreachable. Maybe it’s when you realize your “segmented” backup isn’t as protected as you thought.
Or maybe it’s when you’re staring at a situation your plan never imagined could happen.
I’ve been there. Standing in front of executives, incident burning around us, and thinking: “This is not what we practiced.”
The Poll Results Don’t Lie
The LinkedIn poll I posted this week? The results are tracking exactly with what I see in the field. Many of us aren’t actually confident our plans would work when it matters.
And honestly? That gut feeling is probably right.
The Question That Keeps Me Up
Here’s what haunts me: What if the thing we think will save us is actually making us more vulnerable?
What if our incident response plans, the beautiful, framework-mapped, annually-updated documents we’re so proud of, are giving us a false sense of security about scenarios we can’t even imagine?
I’ve found something in my research that I can’t unsee. A pattern in how the most devastating incidents unfold. A common thread in why organizations with “good” IR plans still fail catastrophically.
And it’s not what you think.
Why This Matters Now
I’m not just talking about working long weekends or looking bad in front of executives. The stakes are literally life and death in some cases. The examples I’ve been digging into for my ISC2 talk have kept me awake at night.
But here’s the thing: this is fixable. There’s a way to approach incident response that actually prepares you for chaos instead of just checking compliance boxes.
What’s Next?
I can’t fit everything into a blog post (trust me, I tried). But I can tell you this: if you think your IR plan will work when everything goes sideways, we need to have a conversation.
I’m sharing the full story, the research, the patterns, the solutions that actually work, at ISC2 Security Congress on October 28.
Because that uncomfortable silence when I asked about actually using IR plans? It’s telling us something important.
And it’s time we listened.
Register for ISC2 Security Congress with code NETWORK25SC for 15% off. Some conversations can’t wait. → Learn more about my speaking topics
Currently available for CISO and Head of Security roles (full-time, fractional, or advisory). If your organization needs someone who’s seen what happens when theory meets reality, let’s connect.
This is the first post in a series about Incident Response. You can read the next post here
Ready to Secure Your Growth?
Whether you need an executive speaker for your next event or a fractional CISO to build your security roadmap, let's talk.
Consulting services are delivered through Vaughn Cyber Group.
Related Posts

When Perfect Plans Meet Imperfect Reality
Sometimes the consequences of IR plan failure aren't just about downtime or data. Sometimes they're about life and death.
Automating Ourselves Into a Cybersecurity Crisis
How AI automation in cybersecurity is eliminating entry-level roles and creating a dangerous skills gap, and why we must act now to prevent a workforce crisis.

Why Your Incident Response Plan Will Fail (And What to Build Instead)
Most IR plans fail not because they're poorly written, but because plans don't survive contact with reality. Here's how to build response capability instead of just documentation.
